This post is the first in our content series on exploring the risks of non-compliance with security, financial, architectural, or vendor requirements when deploying mission/business-critical systems and data to the cloud. In this series we will analyze risk events and their potential impacts on organizations and people. We will also discuss how using OpsCompass would have identified the risk conditions before any exposure became a problem. We will clearly cite public information, and when our customers have avoided threats through the use of our monitoring solutions, we will protect their identities and details.
What was the Exposure Event?
In an article at defensescoop.com, a critical data exposure of sensitive U.S. military information was disclosed. This event not only has the potential for a huge negative impact on the United States, but on every country and citizen worldwide. According to the article:
“Security researcher Anurag Sen reportedly discovered the exposure this weekend and flagged it to TechCrunch, the first publication to report on the incident — which it did after notifying the Pentagon. Sen regularly seeks out and works to safeguard open databases and vulnerable servers holding information that might be sensitive to national security. ‘I found out about [this exposure] during a routine check,’ Sen told DefenseScoop on Tuesday.
security researcher, anurag sen
“What was probably a misconfiguration issue — likely associated with a human-made error, according to Sen — enabled any person who knew the correct IP address to access certain sensitive military messages and data by typing the code into an internet browser.
“‘It was that simple,’ the cybersecurity researcher said.”
It is unfortunate, but true, that most risky vulnerabilities we encounter are simple misconfigurations. In our analysis of this situation there were two major issues in the configuration of these military servers that should have been identified and remediated before ever being deployed:
- The server setup did not require a password for access, and
- The server was configured to allow connections from and to the Internet.
John Grange, OpsCompass CTO, performed the analysis on this data exposure and made the following comments:
“This sort of error is extremely common in the cloud, whether private or public sector. Because the use of cloud infrastructure is so ubiquitous, attackers aren’t even wasting time anymore with traditional attacks like SQL injection and password dictionary attacks. They are hunting for misconfigured cloud resources and compromised authentication credentials. They might obtain these in public git repos as well as via phishing attacks.
OPSCOMPASS CTO, John grange
“In this situation, I am actually surprised that this article as well as others referenced in it did not highlight the fact that it was not just that the server was setup incorrectly to not require a password, but that it was also accessible directly via the Internet. So, the operating system on the virtual machine was misconfigured by not setting up user authentication, but it was also misconfigured on the cloud platform side to allow connections to and from the Internet. There were two layers of misconfiguration, one at the workload layer and the other at the cloud platform layer.”
What is the Potential Impact?
In a follow up article on defensescoop.com, a U.S. Pentagon spokesperson acknowledged the data exposure, and indicated that they were still trying to determine if any data sources were compromised, and what the potential impact would be.
“In an email Thursday night, DOD spokesperson Cmdr. Jessica McNulty told DefenseScoop that the Pentagon is diving deep into the ‘potential exposure of DOD unclassified, commercially cloud-hosted data to the Internet over the past two weeks’ — and that the ‘affected server was identified and removed from public access on’ Feb. 20.
“‘U.S. Cyber Command and Joint Force Headquarters-Department of Defense Information Network (JFHQ-DODIN) continue to work with affected DOD entities and the Cloud Service Provider to assess the scope and impact of this potential data exposure,’ McNulty told DefensesScoop on Thursday.”
DOD Spokesperson, Cmdr. Jessica McNulty
It would be impossible at this point to try to quantify the potential cost or risk of such an exposure and potential disclosure. Considering that the email contained “sensitive military data” it is fair to say that the potential negative impact is astronomically huge. So, is it possible to find even these “simple misconfigurations?”
How Would OpsCompass have Identified the Problem?
OpsCompass would have absolutely found all of the virtual machines in the environment that had public access enabled. In OpsCompass, customers not only see how many virtual machines are misconfigured in this way, but we provide explicit instructions for how to remediate the issues that were found.
The following screenshots from OpsCompass illustrate how we identify the issues, and then raise the priority to ensure the most critical vulnerabilities are addressed first.
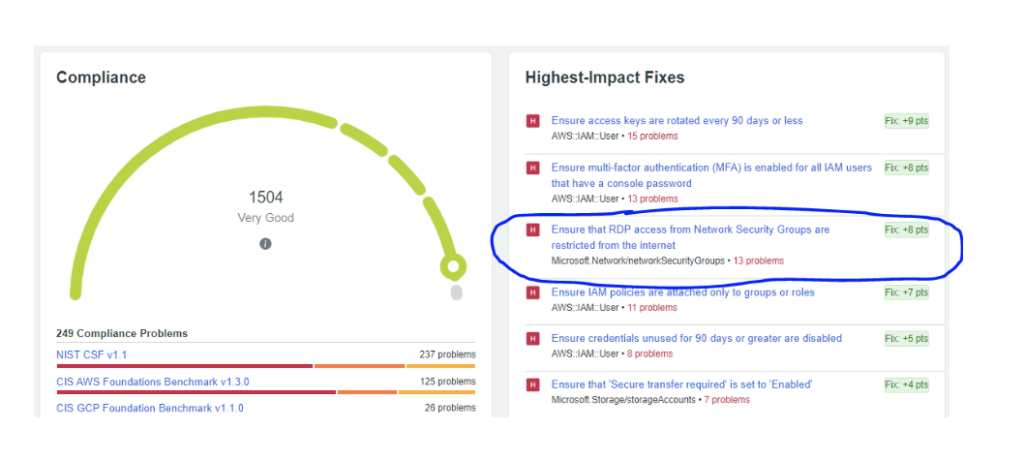
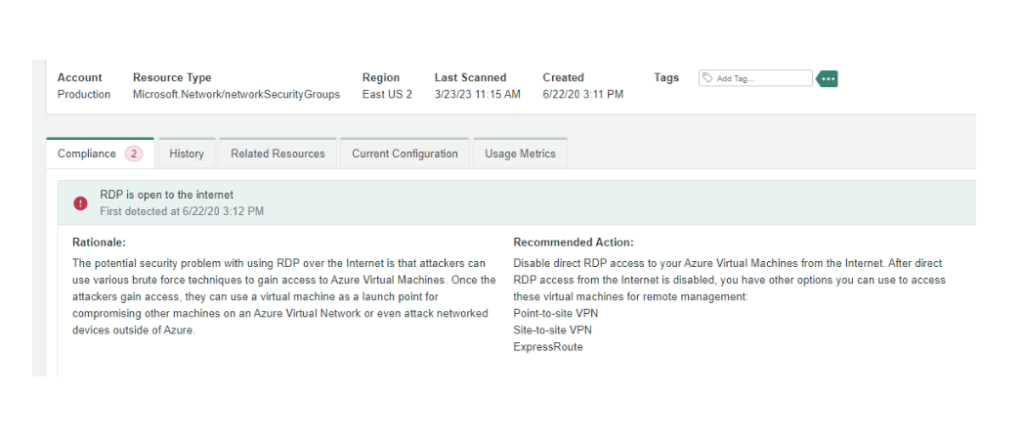
While we do not know how the data was stored in the Azure VM, if it was a SQL Server or Oracle database, OpsCompass would have gone deep into the database configurations to identify vulnerabilities such as missing user authentication requirements, or anonymous access availability. OpsCompass performs table-level security checks on the database itself.
A powerful innovation included with OpsCompass is the ability to not only identify misconfigurations, but to also check for how those configurations change or drift over time. It is possible that a cloud environment will be secure when it is deployed, but through subsequent changes critical vulnerabilities are unknowingly introduced. OpsCompass takes a high-fidelity snapshot of the original cloud environment and tracks every configuration drift that occurs. We analyze and log those drifts for security and cost vulnerabilities and alert the user to critical conditions that require remediation.
Summary
As the U.S. Pentagon, and all OpsCompass customers have learned, even small misconfigurations in cloud environments and databases can result in potentially catastrophic outcomes. OpsCompass watches your cloud and database environments to proactively identify threats and potential cost overruns. Sign up for a free trial or contact us if you would like to learn more. Sign up for our newsletter to receive notifications of our next risk analysis content.







