Andy Kerber (@dbakerber), Senior Consultant
As an Oracle DBA, I often find it necessary to use X-Windows. For unknown reasons, Oracle has chosen to standardize on X-Windows as the normal installer for their software. Because of this requirement for Oracle, those who want to install Oracle products in AWS need to be able to run X-Windows on their EC2 instances. In this post, we will cover the process of installing the required software on the EC2 instance and configuring PuTTY on your desktop for use with X-Windows on the AWS EC2 instance.
Our chosen SSH software is PuTTY, which has an option to allow X-Windows forwarding on port 22. Thus, we know that port 22 is the port we will need in order run the Oracle installer. Most of these same steps are required for other software such as MobaXterm, though MobaXterm will not use PPK files.
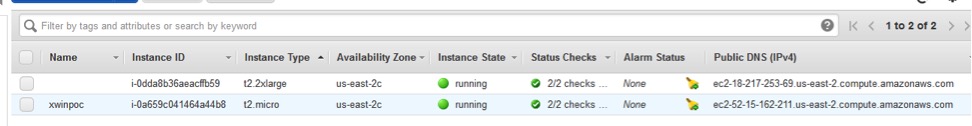
First, create an EC2 instance using RHEL 7. Others may work, but RHEL is a standard operating system that most people are familiar with. We have two EC2 instances configured, but for the purposes of this exercise we are concerned with the second:
When you created the EC2 instance, a private key file (suffix .pem) was also created. We need to convert this to a .ppk (PuTTY private key) file. It is a fairly easy process, as shown below.
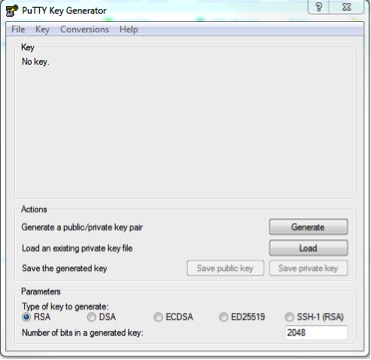
1. Install PuTTY if you have not already done so. Run the full install so that PuTTYgen is installed
2. Start PuTTYgen
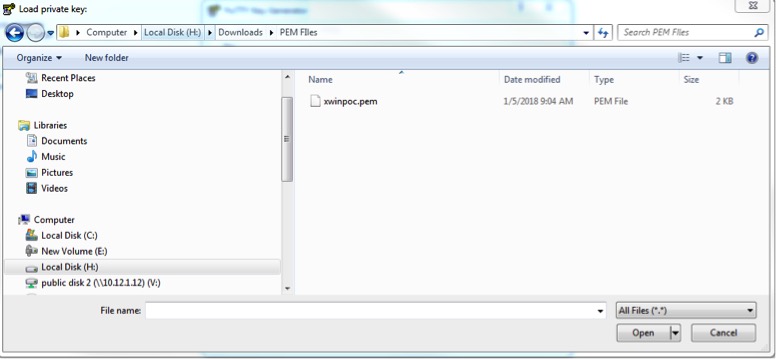
3. Click load, and load the .pem file downloaded from AWS. Note that you will need to change the default file type to all files (from .ppk)
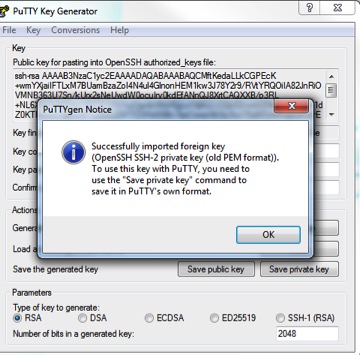
4. In PuTTYgen, follow the instructions to generate the PPK file.
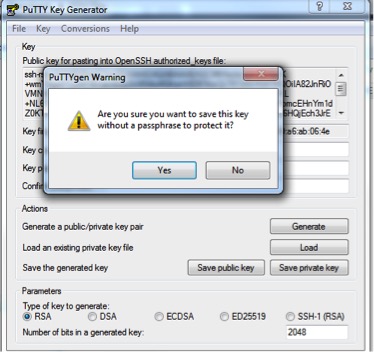
5. Save the file without a passphrase.
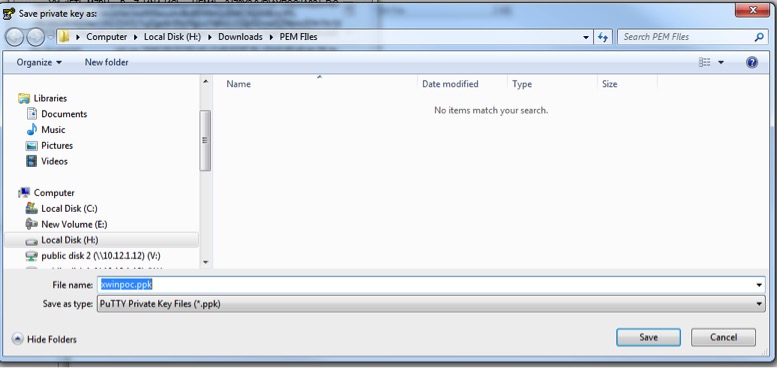
6. Choose an appropriate name and save the file.
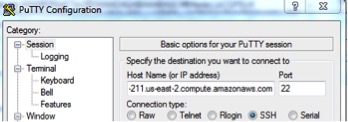
7. Now start PuTTY and configure the connection. In the hostname field, put ec2user@<public dns name>, eg ec2-user@ec2-52-15-162-211.us-east-2.compute.amazonaws.com:
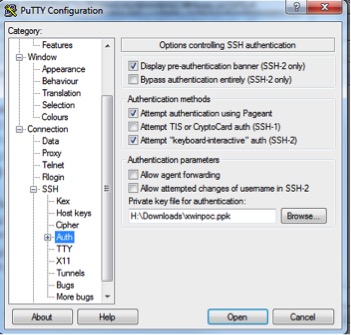
8. In the SSH auth section, accept the defaults, and insert the fully qualified path and file name for your PPK file in the private key file section:
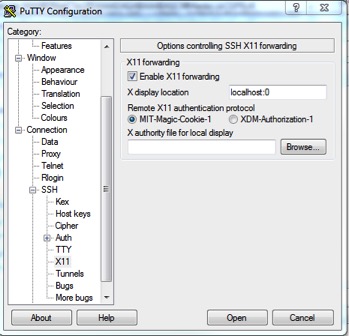
9. In the X11 section, choose ‘Enable X11 forwarding’ and localhost:0 for the X display location.
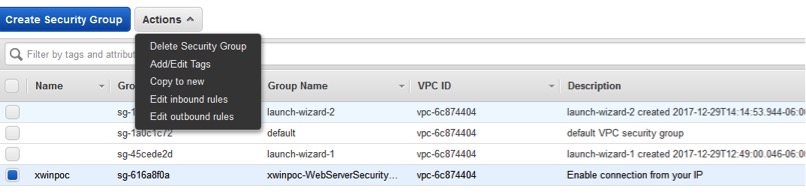
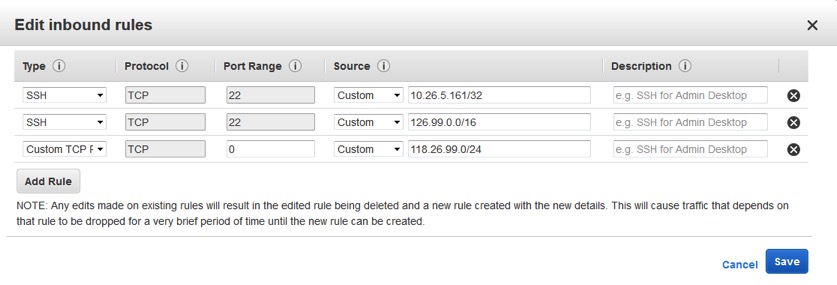
10. Next, back on AWS, you need to configure the AWS firewall to allow you to access your EC2 instance via SSH. To do this, select ‘Security Groups’ on the console, and then on the actions menu, choose edit inbound rules:
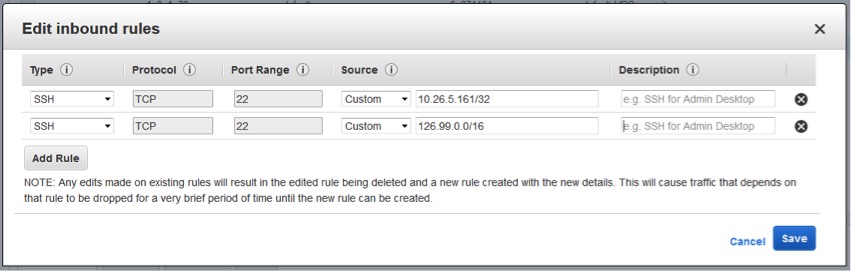
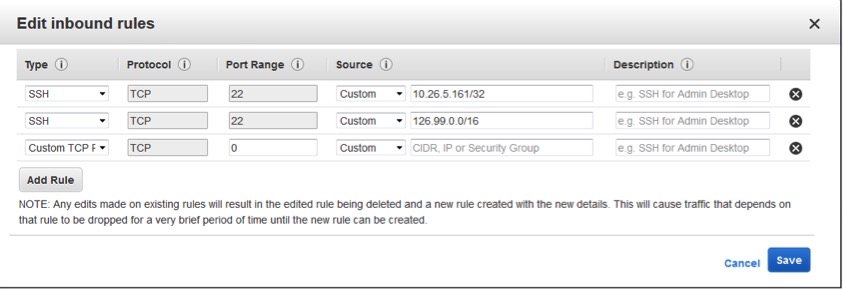
11. Click add rule.
12. Add the appropriate source IP and net mask:
Note that if you are connecting from home, chances are that you have a dynamic IP on your home router, and you will need to find out the range of that dynamic IP. In the example shown, we expect that we will always be connecting from an IP address where the first three octals are 118.16.99, and the fourth set is dynamic, so we have a mask of 24. Your public IP address will not start with 172, 10, or 198. Those are the starting octets for private ranges.
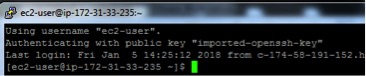
13. At this point, you are ready to connect. To verify your connection, use the PuTTY configuration described above and connect to the EC2 instance. Note that you will connect as the ec2-user.
14. Now, as the ec2-user, sudo to root. ‘sudo su –’.
15. Install the packages that are needed for X Windows:
yum install xorg-x11-xauth
yum install xclock xterm
16. On your desktop, ensure that you have an X-Windows server installed. We are using Xming, and installation instructions can be found here.
17. Next, start a new session. When you start your first session after installing the X-Windows software, you should see this line:
/usr/bin/xauth: file /home/ec2-user/. Xauthority does not exist.
It will create that file.
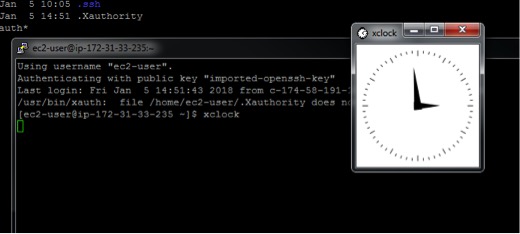
18. Start XMing on your desktop.
19. Type xclock or xterm in your PuTTY session. The xterm or xclock should then open on your desktop after a few seconds:
20. At this point, you have X-Windows working on your AWS EC2 instance. You can now proceed with installing Oracle, or any other software that uses X-Windows as its installation method.
In this post, we have covered the process of installing required software on your EC2 instance and configuring PuTTY on your desktop for use with X-Windows on the AWS EC2 instance.